Quick take:
- NFT scam is one of the biggest drawbacks of the exciting world of Web3.
- One NFT enthusiast in a long thread of tweets demystifies the tricks that scammers use to lure unsuspecting traders.
- User @0xfoobar also explores a new airdrop offer that dropped in their wallet from an unknown collection.
The non-fungible token (NFT) industry has come into one of the biggest trends of the last 18 months. However, just like any other internet-based industry, it could not evade the drawbacks that scourge the web.
NFTs are digital files created using blockchain technology to provide proof of ownership and authenticity. Yet, cybercriminals continue to exploit the industry’s nascent state of development by stealing from unsuspecting users.
While some Web3 startups have created solutions and firewalls to flag suspicious activity on their platforms, that has not been enough.
But all is not lost as some startups continue to take a specialised view of the situation by creating services that are tailor-made to curb scams from the industry.
Recently Chainalysis raised $170 million to create an NFT detection product that will help reduce scams in the industry, while FTX backed NFT fraud detection service provider Doppel’s $5 million funding round.
Earlier this year, NFTgators cited a UK report that showed NFT fraud rose 400% in 2021 amid the rapid growth of the industry fueled by the influx of celebrities and venture capital funding.
But the fight is not left to the corporations alone. NFT enthusiast @0xfoobar in a long thread of tweets tries to demystify NFT fraud by exploring a new NFT airdrop offer that dropped in their wallet from an unknown collection.
“I got an NFT airdrop from an unknown collection into my wallet with a 1 WETH offer. What’s going on? Is it safe to accept?”, in a Twitter thread titled: “Exploring the Latest FT Scam”.
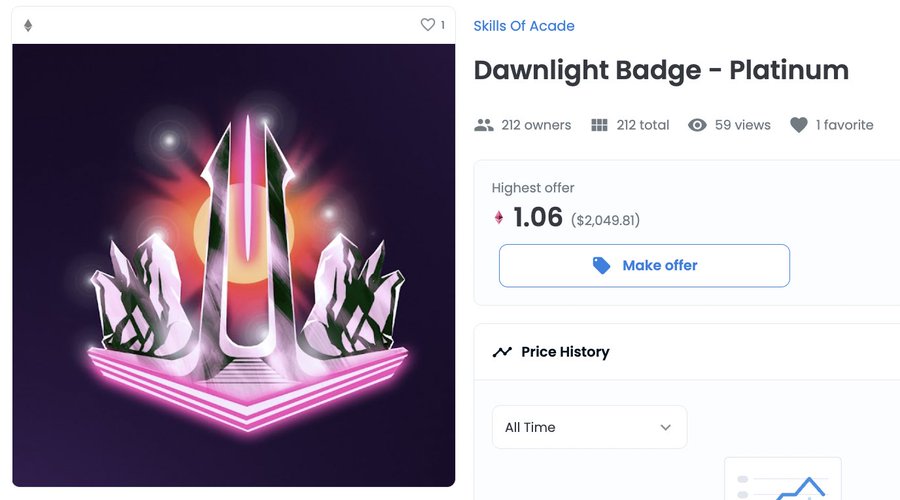

The offer would cost the trader 1.06 WETH, equivalent to $2,049.81 as per the screen capture.
The trader tries to explain how the scams work by using the example of OpenSea, the world’s largest NFT marketplace.
“The way that OpenSea works is through “approvals” to transfer your NFTs or your WETH’” Foobar wrote.
In such a circumstance, this scam would only work if the marketplace the offer is on is untrustworthy itself.
This is dangerous! But only in one direction. If the marketplace is malicious, it can steal your money/jpegs. But if the money/jpegs are malicious, they *cannot* steal your marketplace.
The trader argues that if a marketplace’s security protocols are not strong enough, it can let one approved collection steal another approved collection.
“A single malicious signature can rug *all* of your approved OpenSea NFTs. No need to sign an individual sell order for each one, as originally assumed.”
Foobar cites the February 20, heist that saw a hacker steal 10 Azukis, 3 Mutant Apes and other NFTs in one transaction.
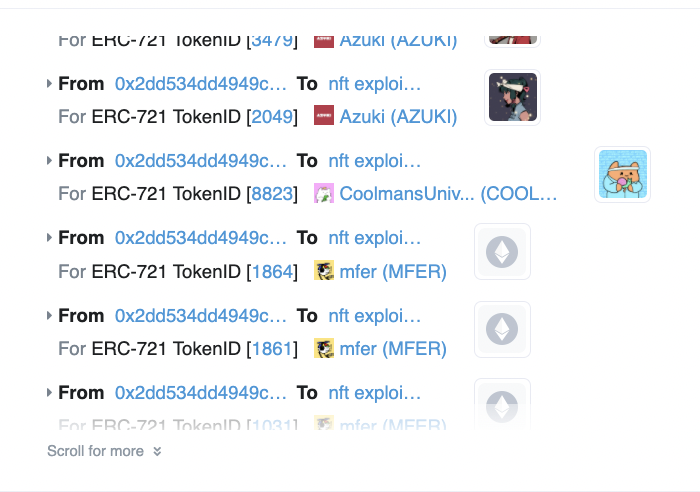

Thus, the best course of action when making NFT transactions is to “approve an external contract to spend your money/jpegs by making a call to the money/jpegs contract— and not by making a call to the external contract,” the trader wrote.
Foobar believes that it could be “theoretically “safe” to interact with a malicious contract, as long as your transactions are going directly to the malicious contract and you’re not sending any raw ETH to payable functions*.”
However, there is a strong warning to go exploring this possibility because it is possible to make the mistake of thinking you are interacting with an external contract when, in fact, you are interacting with your own jpegs contract.
“A website might say, “click here to animate your ape” but the wallet transaction will say “SET APPROVAL FOR ALL” he warns.
Foobar provides two ways that hackers will try to explore if they cannot get hold of your wallet of assets.
- They can embed a malicious URL at the point of contract approval where traders click to accept an offer. The trap comes in the form of an error message carrying a malicious URL.
- The NFT offered can be a proxy contract that could be swapped for a different use case later. Foobar points to an address that “receives dust from 260 separate addresses that each created one proxy contract pretending to be a unique collection.” https://etherscan.io/address/0x2d1a138f2cb7962d5a270d0c07ea9ea4b59348a5.
Stay up to date: